Sitemap
A list of all the posts and pages found on the site. For you robots out there, there is an XML version available for digesting as well.
Pages
Posts
Future Blog Post
Published:
This post will show up by default. To disable scheduling of future posts, edit config.yml and set future: false.
Blog Post number 4
Published:
This is a sample blog post. Lorem ipsum I can’t remember the rest of lorem ipsum and don’t have an internet connection right now. Testing testing testing this blog post. Blog posts are cool.
Blog Post number 3
Published:
This is a sample blog post. Lorem ipsum I can’t remember the rest of lorem ipsum and don’t have an internet connection right now. Testing testing testing this blog post. Blog posts are cool.
Blog Post number 2
Published:
This is a sample blog post. Lorem ipsum I can’t remember the rest of lorem ipsum and don’t have an internet connection right now. Testing testing testing this blog post. Blog posts are cool.
Blog Post number 1
Published:
This is a sample blog post. Lorem ipsum I can’t remember the rest of lorem ipsum and don’t have an internet connection right now. Testing testing testing this blog post. Blog posts are cool.
portfolio
Ciphercraft
This library is an open-source java library that allows for secure multi-party computation, and is flexible for various uses such as indoor localization, drone collision avoidance and decision tree evaluation. 
Treespace Working Group - Python scripts
This code computes metrics for rooted phylogenetic networks 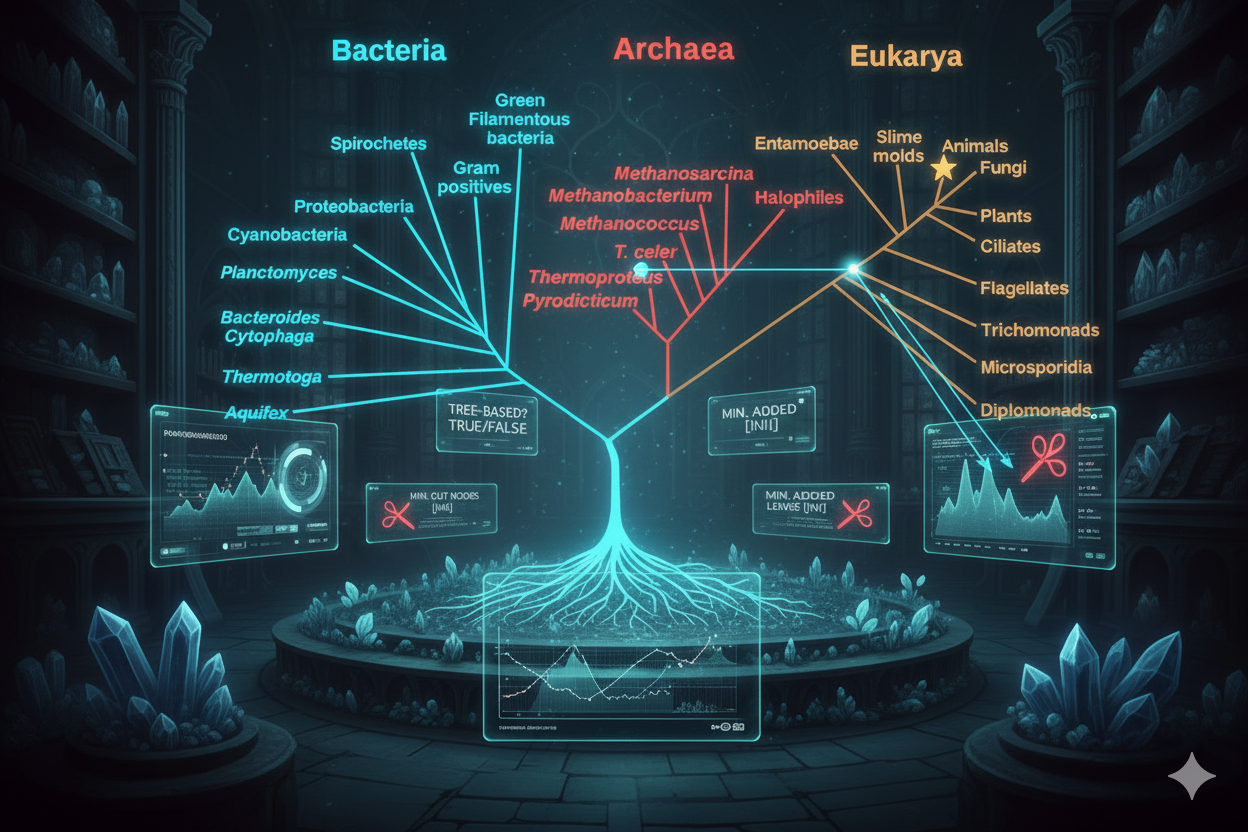
LAVA: Large Scale Automated Vulnerability Addition
This is an area of research interest on planting realistic security bugs in C. 
IoT Inspector
This is the topic of my PhD Research, the idea is to analyze IoT network traffic, and utilizing labeled network traffic, derive user behavioral and health insights. 
Risk Evaluation Assessment Plugin (REAP)
This is an MBSE plug-in used to more accurately measure compliance with security controls. Also, it can provide insight via simulations on how likely a network would fare under cyber attack, given data of an organization’s cybersecurity controls. 
Platform Architecture Neutral Dynamic Analysis (PANDA)
PANDA is used for dynamic analysis for analyzing how binaries work using a deterministic record and replay. PANDA has plug-ins that allow for in-depth analysis such as being able to track input bytes usage in a program. 
publications
Server-side Fingerprint-Based Indoor Localization Using Encrypted Sorting
Published in IEEE Mobile Ad Hoc and Sensor Systems (MASS), 2019
This paper is about secure indoor localization using homomorphic encryption. We compare an approach of sorting encrypted numbers at the server compared to decrypting at the client phone. While decrypting at the server is slower, it does save some battery for the client
Recommended citation: Quijano, Andrew, and Kemal Akkaya. "Server-side fingerprint-based indoor localization using encrypted sorting." 2019 IEEE 16th International Conference on Mobile Ad Hoc and Sensor Systems Workshops (MASSW). IEEE, 2019.
Download Paper | Download Slides | Download Bibtex
Maximum Covering Subtrees for Phylogenetic Networks
Published in IEEE/ACM Transactions on Computational Biology and Bioinformatics (TCBB), 2020
This paper solved an open question about the minimum number of nodes to remove from a phylogenetic network N to make it tree-based.
Recommended citation: Davidov, Nathan, et al. "Maximum covering subtrees for phylogenetic networks." IEEE/ACM Transactions on Computational Biology and Bioinformatics 18.6 (2020): 2823-2827.
Download Paper | Download Bibtex
Out of Our Depth with Deep Fakes: How the Law Fails Victims of Deep Fake Nonconsensual Pornography
Published in Richmond Journal of Law and Technology, 2021
This paper discusses deep fake nonconsensual pornography, and the need for Section 230 revision as copyright law would not provide sufficient protection to victims
Recommended citation: Kate Kobriger, Janet Zhang, Andrew Quijano & Joyce Guo, Out of Our Depth with Deep Fakes: How the Law Fails Victims of Deep Fake Nonconsensual Pornography, 28 Rich. J.L. & Tech 204
Download Paper | Download Slides | Download Bibtex
Privacy-Preserving Drone Navigation Through Homomorphic Encryption for Collision Avoidance
Published in IEEE Local Computer Networks (LCN), 2024
This paper implements the line intersection algorithm using partially Homomorphic encryption. This approach leads to much faster performance and maintain privacy of the paths of two drones.
Recommended citation: Luedeman, Allan, et al. "Privacy-Preserving Drone Navigation Through Homomorphic Encryption for Collision Avoidance." 2024 IEEE 49th Conference on Local Computer Networks (LCN). IEEE, 2024.
Download Paper | Download Slides | Download Bibtex
Enhanced Outsourced and Secure Inference for Tall Sparse Decision Trees
Published in IEEE - International Performance Computing and Communications Conference (IPCCC), 2024
This paper is about implementing a privacy-preserving decision tree, but in the case of tall sparse decision trees. To improve performance, we minimize number of encrypted integer comparisons while also generally preserving timing attack resistance
Recommended citation: Quijano, Andrew, et al. "Enhanced Outsourced and Secure Inference for Tall Sparse Decision Trees." 2024 IEEE International Performance, Computing, and Communications Conference (IPCCC). IEEE, 2024.
Download Paper | Download Slides | Download Bibtex
Reap the Rewards: Bridging Risk Assessment and Secure Application Development Practices
Published in INCOSE Symposium 2026, 2025
This paper leverages using Model Based Systems Engineering (MBSE) to create a more systematic approach to measuring cyber risk. This also goes over the creation of an MBSE plug-in, Risk Evaluation Assessment Plugin (REAP), which can help simulate cyber risk and RTO/RPO compliance
Recommended citation: Quijano et al. "REAP the Rewards: Bridging Risk Assessment and Secure Application Development Practices" INCOSE Symposium 2026
Download Paper | Download Bibtex
talks
Columbia University Alumni Panel - Discussion on working in Tech
Published:
I talked with four other Columbia Alumni about careers in tech.
Privacy-Preserving Drone Navigation Through Homomorphic Encryption for Collision Avoidance
Published:
I presented my paper on secure collision avoidance here at the IEEE LCN conference in the Special Track Papers: Algorithmic Solutions for Drone- and Robot-based Networks (ASDRoNet)
PhD Qualifying Exam
Published:
As of August 21st, I finally became a PhD candidate! I combined my two papers published in 2024 to show I meet the bar to start working on my dissertation under Danny Huang.
Privacy Day Poster Session
Published:
Cornell Tech hosted Privacy Day. I created a poster based on my work on secure indoor localization.
teaching
Columbia University - all course assistant experience
Class, Columbia University, Computer Science, 2019
This post will go over my experience as a course assistant at Columbia University from Fall 2018 to Fall 2021, this post will go over my experience as a course assistant at Columbia University.
Application Security - New York University
Class, New York University, Computer Science and Engineering, 2023
I was an Adjunct Professor for the Cyberfellows Application Security course for the following semesters: Spring 2023, Fall 2023, Spring 2024.
